- Secure Network using Cisco Port Security, Part 1: Concept
- Secure Network using Cisco Port Security, Part 2: Configuration
From the previous, you know basic concept about Port Security. Now let’s see it in the real action.
Step-by-step for configuration port security
- Telnet to the switch.
c:\telnet 10.0.0.1
- Enter configuration mode.
switch#config t
- Enter interface configuration mode. I’m going to enable port security on the first interface (GigabitEthernet 0/1).
switch(config)#interface GigabitEthernet 0/1
- Sets the interface mode as access.
switch(config-if)#switchport mode access
- Enables port security on this interface. When you’ve enabled port security, all the connection on the interface
switch(config-if)#switchport port-security
Note:When you’ve enabled port security, all connections on this interface will be resetted so don’t try to enable on a working interface.
- Set the maximum number of secure MAC Addresses on the interface to 2. Some interfaces may have more than a device connected to. Default is 1.
switch(config-if)#switchport port-security maximum 2
- Set the violation mode to restrict. For more information about violation mode, see Port Security Options section above.
switch(config-if)#switchport port-security violation restrict
- If there is any device connected to this interface, the switch will learn and insert into Secure Mac Address Table. This is Dynamic secure MAC Addresses. These MAC Addresses will be removed if the port shut down or the switch restarts.
To view the current Secure Mac Address Table, exit the configuration mode and enters the command below.switch(config-if)#exit switch(config)#exit switch#show port-security interface GigabitEthernet 0/1 address
Note: If the port shuts down, all dynamically learned addresses are removed.
You’ll see the figure as below. This example has 2 PCs connect to the interface so there are 2 MAC Addresses on the table. It may takes some time for the switch to learn MAC Addresses.
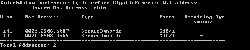
- After the interface has reached the maximum number of secure MAC Addresses. In this example is 2. No more devices can access the network’s resource anymore. To check if there is any violation on the interface, type the command below.
switch#show port-security interface GigabitEthernet 0/1
In this example, I have connected a third device to the interface so you’ll see the last line Security Violation Count. If this value is more than 0, then there is a violation occur on the interface.
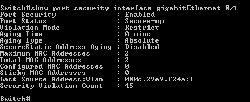
- If you want MAC Addresses to be deleted after a period of time from the Secure Mac Addresses Table, you’ll have to set aging of the interface. In this example, I’m going to set to delete a MAC Address after no activity of the device for 5 minutes.
switch#conf t switch(config)#interface GigabitEthernet 0/1 switch(config-if)#switchport port-security aging type inactivity switch(config-if)#swtichport port-security aging time 5
- View Secure Mac Address Table again. You’ll the Remaining Age is change to 5 (I) which I indicates inactivity type of aging. So if there is an inactivity device for 5 minutes, the MAC Address of the device will be removed from the Secure Mac Address Table.
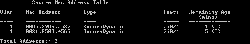
- You can add a Static secure MAC Address by type the command below.
switch#conf t switch(config)#interface GigabitEthernet 0/1 switch(config-if)#switchport port-security mac-address 000C.29E9.F24A
- To enable sticky learning, type the command below.
switch(config-if)#switchport port-security mac-address sticky
When you’ve enabled sticky learning, it converts the dynamic MAC addresses to sticky secure MAC addresses and to add them to the running configuration automatically.

- Now when you want to add a new device to the interface, you only have 2 options: delete one sticky secure MAC Address or increase maximum allowed secure MAC Addresses.
To delete one sticky secure MAC Address,switch(config-if)#no switchport port-security mac-address sticky 000c.29e9.f24a
To increase maximum allowed secure MAC Addresses
switch(config-if)#no switchport port-security maximum 3
- Next, to disable sticky learning.
switch(config-if)#no switchport port-security mac-address sticky
- To disable port security
switch(config-if)#no switchport port-security
Summary
Port Security can protect network from unauthorized access efficiency (if it is applied properly). But it requires some work for administrator. For example, add/remove secure MAC Addresses in sticky secure MAC Address type. There is also another way to implement Network Access Control by implement IEEE 802.1X which authenticate through RADIUS server.
Thanks….
Beware; on our network we’ve discovered a bug with port-security. When enabled it takes 3 seconds between putting the MAC-address in the mac address-table and forwarding the first packet.