- Getting Started with Forefront Threat Management Gateway 2010, Part 1: Introduction
- Getting Started with Forefront Threat Management Gateway 2010, Part 2: Planning
- Getting Started with Forefront Threat Management Gateway 2010, Part 3: Prepare Your Server
- Getting Started with Forefront Threat Management Gateway 2010, Part 4: Sample Deployment Scenarios
- Getting Started with Forefront Threat Management Gateway 2010, Part 5: Installation
- Getting Started with Forefront Threat Management Gateway 2010, Part 6: Configuration Wizard
- Getting Started with Forefront Threat Management Gateway 2010, Part 7: Web Access Wizard
Planning
Before we start Forefront TMG 2010 implementation, we should have a plan in order to make installation and configuration processes go smoothly as much as possible.
Note: It is still recommend to read official documentations from Microsoft, such as, getting started guides, release notes because there might be some important details specifically for your case that I haven’t mention in this series.
In this part, you will see what you should know and decide before implement Forefront TMG 2010:
- Hardware and Software Requirements
- Network Topology
- Type of Clients
Hardware and Software Requirements
Hardware Requirements
You can check System requirements for Forefront TMG which has officially been released by Microsoft which describes minimum hardware and software requirements. However, we shouldn’t rely only the minimum system requirements to build our system because each system has different environment and condition. Here are recommended hardware requirements for implement forefront TMG 2010 as Secure Web Gateway:
| Hardware / User | < 500 | 500 – 1000 | 1000 – 1500 | 1500 – 2000 | 2000 – 3000 | |
|---|---|---|---|---|---|---|
| CPU | Dual Core | Quad Core | Quad Core | 2 x Quad Core | 2 x Quad Core | |
| Note: Forefront TMG is designed to run only on x64-capable processors. It will not run on Itanium-based systems. | ||||||
| Memory | 4 GB | 8 GB | 8 GB | 8 GB | 12 GB | |
| Harddisk | System | Holds OS and program files, approximately 40 GB. | ||||
| Log | 50 GB | 100 GB | 150 GB | 200 GB | 250 GB | |
| Cache | The recommended maximum size of a cache file is 40 GB per physical disk drive. | |||||
| Note: Space for logging is calculated for 3 days in addition to the current day. Estimate that each user creates about 25 MB of logs per day for web traffic. It is recommended that you store logging and web cache in separate harddisk from the OS. | ||||||
| Network Interface Card (NIC) | Recommend: 1 Gigabit Ethernet adapter. The number of adapters depend on network topology deployed in your network. | |||||
Note: If you have different deployment scenarios from above, for instance, number of users > 3000, or plan to deploy Forefront TMG 2010 as proxy server or secure mail gateway, you can read Forefront TMG 2010 hardware recommendations which will cover more deployment scenarios.
Software Requirements
Here is the table of software requirements for Forefront TMG 2010. You only need to install Windows Server by yourself, others will be installed by Forefront TMG 2010 automatically on preparation step which you will see in the installation part.
| Software | Minimum Requirements |
|---|---|
|
Operating system |
Windows Server 2008
|
|
Windows Roles and Features |
These Roles and Features are installed by the Forefront TMG Preparation Tool:
You can run the Preparation Tool from the Forefront TMG autorun page. |
|
Other software |
Note: Services and driver files installed by Forefront TMG are placed in the Forefront TMG installation folder. |
Reference: System requirements for Forefront TMG
Network Topology
Forefront TMG 2010 comes with 4 predefined network templates which you have to select one that is the most suitable for your existing network topology, and for your network security requirements.
- Edge Firewall. This is the common template mostly used by small organizations. Forefront TMG server is located at the network edge and connect two networks together: the internal network, and the external network (usually the Internet). A typical Edge Firewall template requires a minimum of two network interfaces on the Forefront TMG server.
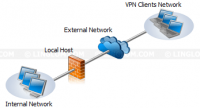
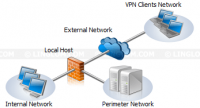
- 3-Leg Perimeter. The 3-Leg Perimeter template is similar to the Edge Firewall except that it has additional network (perimeter network) connects to Forefront TMG server. The perimeter network, also called DMZ (Demilitarized Zone), contains services which can be accessed from the Internet but still be protected by Forefront TMG server. The typical services in DMZ are web servers, FTP servers, DNS servers, etc. This template requires three or more network interfaces on the server.
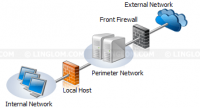
- Back Firewall. This template is used by organizations that security is high priority. In this template, there are more than one firewall. Forefront TMG server is located at the network’s back-end behind a front firewall. A front firewall could be any firewall appliance (hardware/software), but it shouldn’t be same product as the back firewall in order to harden security.
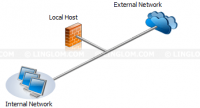
- Single Network Adapter. This template limits features of Forefront TMG server. The Forefront TMG server cannot be used as a real firewall because it is connected to one network only, either the internal network or a perimeter network. It is mostly used as proxy server or caching web content.
After you read all network templates, you have to decide which one would be the best suitable for your organization. Implementing wrong or unsuitable template could reduce network performance and security.
Type of Clients
Forefront TMG 2010 supports 3 types of clients which are SecureNAT client, web proxy client, Forefront TMG client.
- Secure network address translation (SecureNAT) client. SecureNAT client is configured by set default gateway on network interface of client computer to the IP address of the Forefront TMG server. You don’t have to install any software on client. Therefore, this client type can be used in any operating system that supports TCP/IP protocol which implies every operating system nowadays. This client type supports every protocol. No user authentication supports, only IP address will be logged on the Forefront TMG server.
- Web proxy client. Web proxy client can be configured in web browsers, such as, Internet Explorer, Firefox, Google Chrome, etc. No any other software installation required. You can configure this client type on any operating system which has web browser that support proxy feature. However, only Hypertext Transfer Protocol (HTTP), Secure HTTP (HTTPS), and File Transfer Protocol (FTP) are supported for this client type. This client type supports user authentication.
- Forefront TMG client. This client type requires you to install and configure Forefront TMG client on client computer. The Forefront TMG client is available on Windows so only Windows operating system is supported. Supports every protocol and user authentication.
Here is a table that compares the Forefront TMG clients.
| Feature | SecureNAT client | Forefront TMG Client computer | Web proxy client |
|---|---|---|---|
| Installation required | Some network configuration changes are required | Yes | No, but requires configuration of the Web browser |
| Operating system support | Any operating system that supports Transmission Control Protocol/Internet Protocol (TCP/IP) | Only Windows platforms | All platforms, but by way of the Web application |
| Protocol support | Requires application filters for multiple-connection protocols | All Winsock applications | HTTP, HTTPS, and FTP (download requests) |
| User-level authentication | Only the IP address of the user is sent to the Forefront TMG server. | Forefront TMG Client sends the user’s credentials to the Forefront TMG server with each request. | User credenticals can be supplied in response to requests from Forefront TMG. |
| Server applications | No configuration or installation required | Requires configuration file | N/A |
Reference: About Forefront TMG Clients
What’s Next?
Now you have basic understanding that need to implement Forefront TMG 2010 in your environment, next we can take some action starting from prepare our server for Forefront TMG 2010 installation.
Rich and resourceful manual